Arbitrum Bridge: Is There Really a Vulnerability?

Once again, Arbitrum bridges are in the spotlight as a recent technical write-up has surfaced, revealing potential vulnerabilities within this bridging solution.

A recent blog post from the Twitter account @tincho has sparked discussions by highlighting perceived weaknesses in the Arbitrum-Ethereum bridge.
Breaking Down the Vulnerabilities:
Before diving into the specifics, the blog outlined the basic structure of a bridge:
If you think the @arbitrum bridge is secure, the message traps will make you think twice.
— tincho 🪷 (@tinchoabbate) December 8, 2022
No need to worry though. It's all intended!https://t.co/MzbVIlpQv7
- Data Transmission from L2 to L1: Data is sent from Layer 2 to Layer 1.
- Waiting for an "Incentivized Relayer": A relayer receives the data message and forwards it to Layer 1.
- Execution on Layer 1 (Ethereum Mainnet): The data is processed via smart contracts to facilitate withdrawal from the opposite end of the bridge.
According to the blog, three vulnerabilities are identified at the final stage—data transmission and validation at the receiving end of the bridge. The author also compared these issues with how Optimism handles similar problems, showing a preference for the rival solution.
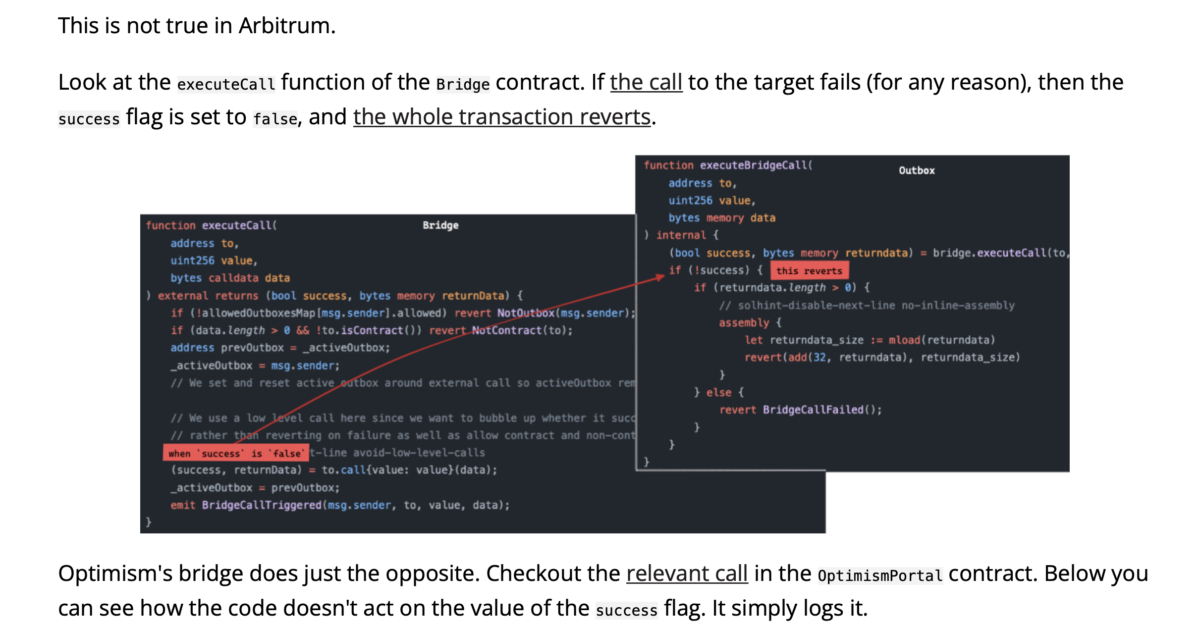
Vulnerability 1: The author argues that the function for validating the "true/false" value in the Execute Call function is exposed, allowing attackers to continuously send "false" data to create loops until their objective is achieved. The author emphasizes that data transmission from L2 to L1 can be "retryable," meaning multiple attempts are possible.
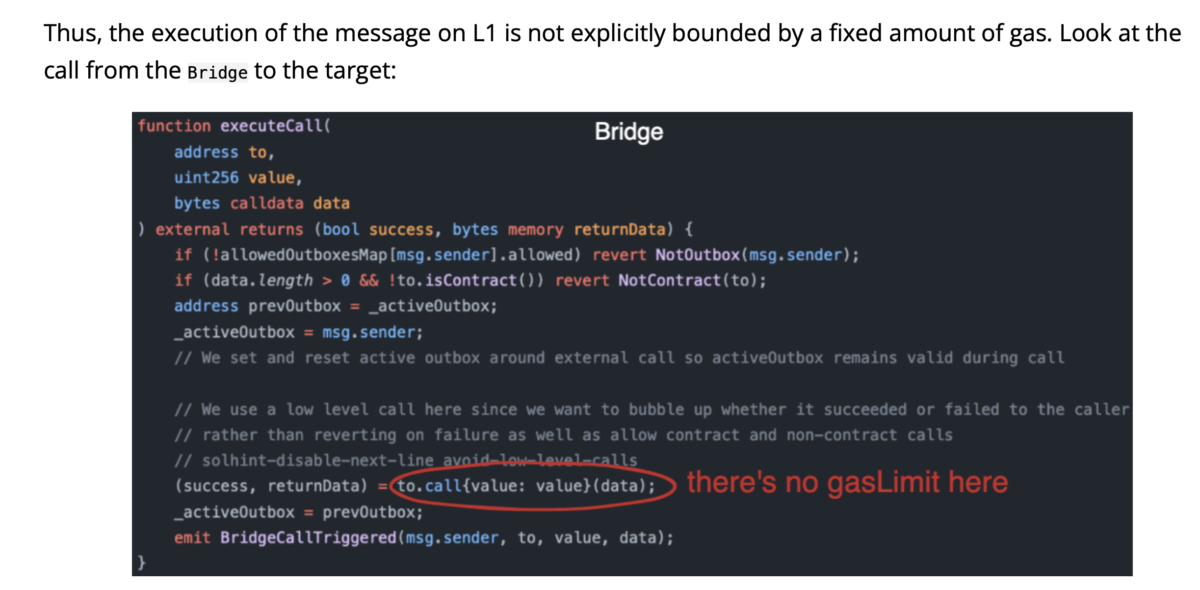
Vulnerability 2: The blog claims that there is no gas limit for data transmission from L2 to L1. This absence of a gas cap could let attackers prioritize their transactions, potentially draining relayers' funds swiftly if issues arise.
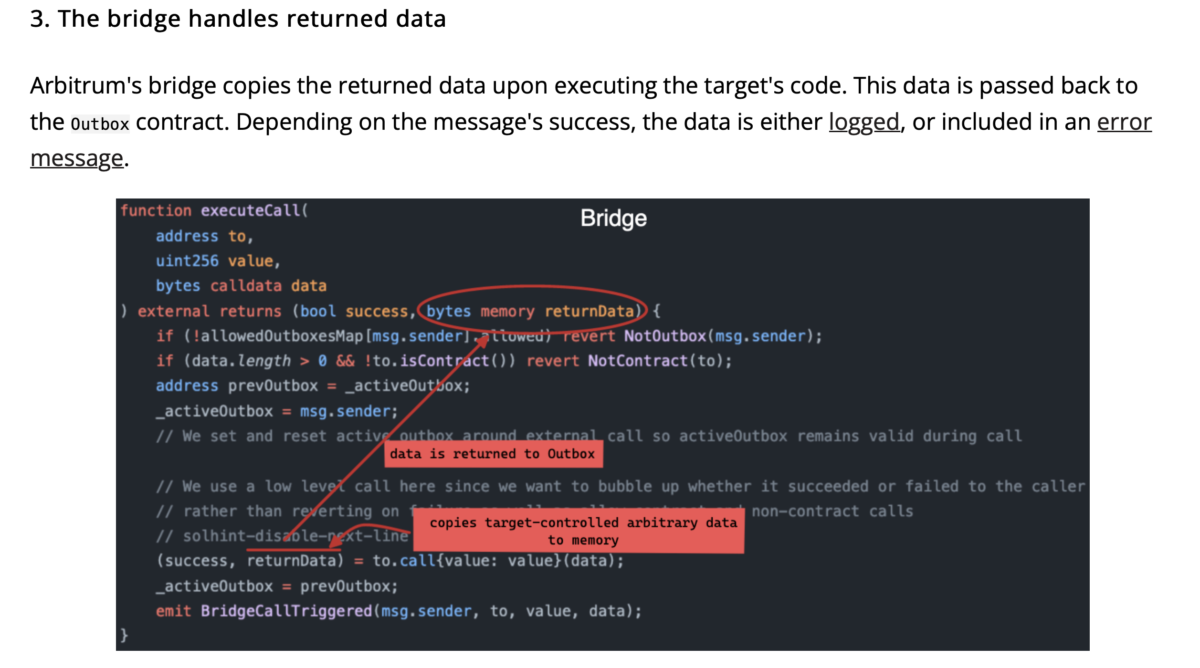
Vulnerability 3: Copying return_Data might cause significant memory storage pressure. Repeatedly copying values into the return_Data variable could create a loop vulnerability, leading to uncontrolled gas fee escalation.
Response from the Arbitrum Team – Are Arbitrum<>Ethereum Bridges Really Buggy?
Quickly addressing these concerns, Arbitrum’s founder and CTO, Harry Kalodner, took to Twitter to clarify the situation.
Regarding concerns about malicious relayers and spam attacks on the Execute Call function, Kalodner stated:
If you think the @arbitrum bridge is secure, the message traps will make you think twice.
— tincho 🪷 (@tinchoabbate) December 8, 2022
No need to worry though. It's all intended!https://t.co/MzbVIlpQv7
"Everyone using the Arbitrum to Ethereum bridge knows that users are expected to withdraw from Ethereum after one week. After this period, users can claim their funds themselves. No third-party relayer interferes with the design or execution."
On the issue of gas limits for data transmission on Layer 2, Kalodner explained:
Anybody who's bridged from Arbitrum to Ethereum knows that we expect users to redeem their own withdrawals on Ethereum after a week.
— Harry Kalodner (💙,💙) (@hkalodner) December 11, 2022
After a week, the user themself “claims” their withdrawal. There are no third party relayers — not in design and not in practice.
"If gas limits were imposed on L2 a week before the transaction, it could make the transaction ineffective, causing user funds to get stuck permanently. Our design fully prevents this scenario."
Summarizing his response, Kalodner stated that the blog’s author based their attack scenario on a "Relayer," an entity almost non-existent in the system. He emphasized that following the author’s recommendations would protect a non-existent relayer while complicating matters for end-users.
Side Notes
After the evening’s discussions, blockchain tech commentator Polynya shared additional advice on using L2-L1 bridges:
As Arbitrum One makes it to #3 across a few key economic activity metrics, now behind only Ethereum and BSC, I'd caution you from using it - it's weakest link (instant upgradability by an opaque 4-of-6 multi-sig) makes it incredibly high riskhttps://t.co/pBrQJune1F
— polynya (@apolynya) December 11, 2022
"With Arbitrum One ranking third in terms of total value locked (only behind Ethereum and BSC), be cautious when using it. The weakest link poses a significant risk: urgent upgrades require only 4 out of 6 multi-sig signatures to pass."
Previously, blockchain tech researcher bartek.eth had posted extensively about data transmission between L1 and L2. Interested readers can check out his threads for a fresh perspective on blockchain network connectivity.
The whole L2 --> L1 message passing mechanism can be summarised on this diagram /14 pic.twitter.com/RkPDcwRknC
— bartek.eth (@bkiepuszewski) December 9, 2022
In September, Arbitrum Nitro (an upgrade of Arbitrum One) discovered a vulnerability in its connection with Layer 1 Ethereum. Thankfully, the issue was addressed promptly, and the white-hat hacker involved has been recognized for their contribution.