Munchables Game on Layer-2 Blast Hacked for $62.5 Million


By noon on March 27, Munchables announced it had reached an agreement with the hacker to recover the stolen funds.
The Munchables developer has shared all private keys involved to assist in recovering the user funds. Specifically, the key which holds $62,535,441.24 USD, the key which holds 73 WETH, and the owner key which contains the rest of the funds.
— Munchables (@_munchables_) March 27, 2024
The stolen ETH has been transferred to a new address.
went into this multisig, looks like we got a fully recovery https://t.co/Ldgd2vPNh8
— 0xngmi (@0xngmi) March 27, 2024
Meanwhile, ZachXBT continues to expose the hacker's connections, alleging that the hacker could be behind several other accounts also working with Munchables.
Four different devs hired by the Munchables team and linked to the exploiter are likely all the same person as they:
— ZachXBT (@zachxbt) March 27, 2024
>recommended each other for the job
>regularly transferred payments to the same two exchange deposit addresses >funded each others wallets
Github Username… https://t.co/Q0scxp6AxK pic.twitter.com/Pjjo4uKXPE
Original Article:
In the early morning of March 27, the X (formerly Twitter) account of the Web3 game Munchables on layer-2 Blast announced that their project had been hacked and assets stolen. Shortly after, on-chain detective ZachXBT traced the hacker's wallet address, revealing that over 17,400 ETH, equivalent to $62.5 million, had been stolen from Munchables.
Munchables has been compromised. We are tracking movements and attempting to stop the the transactions. We will update as soon as we know more.
— Munchables (@_munchables_) March 26, 2024
According to DefiLlama data, Munchables had a TVL (Total Value Locked) of $95.62 million before the attack, which plummeted to $34 million at the time of writing.
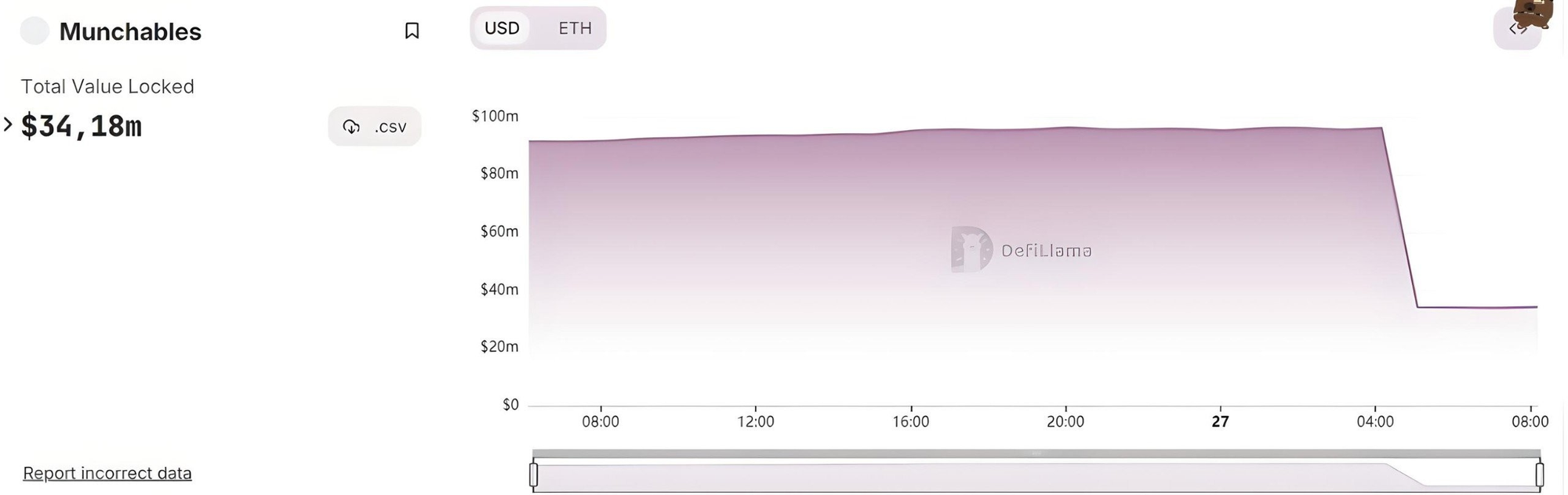
TVL Fluctuation of Munchables. Source: DefiLlama (March 27, 2024)
ZachXBT identified the mastermind as a hacker linked to North Korea, a nation accused of being behind several major crypto project attacks in the past, including Ronin Network, CoinEx, Stake, Atomic Wallet, Harmony, and more.
This is what happens when a North Korean dev is hired
— ZachXBT (@zachxbt) March 26, 2024
not even joking it’s this clown pic.twitter.com/V0Cg4st91t
— ZachXBT (@zachxbt) March 26, 2024
Munchables had hired the hacker, allowing him to infiltrate and modify some lines of code in Munchables' smart contract, granting himself the ability to withdraw assets from the project.
2/ The Lock contract started off with an implementation address of 0x910fFc04A3006007A453E5dD325BABe1e1fc4511
— Quit (@0xQuit) March 26, 2024
This contract is unverified pic.twitter.com/YgpmAof1D7
However, the crypto community on Twitter is currently debating whether Blast should reverse the transactions to restore the assets to Munchables.
The reason for this debate is that Blast is a rollup at stage 0 and extremely centralized, with its bridge to this layer-2 being a multi-sig address rather than a true smart contract. The Blast management team could essentially block the bridge to prevent the hacker from moving assets to other chains and then upgrade the multi-sig wallet contract to nullify the hacker's actions. However, this would expose the centralized nature of Blast, undermining the decentralized philosophy of blockchain and setting a bad precedent.
Technically, the Blast team could recover the $62m lost in the Munchables exploit since they control the bridge contract that holds the bridged ETH/stETH.
— cygaar (@0xCygaar) March 26, 2024
It wouldn't set a good precedent for future exploits/issues, but it is possible.
An invalid state root would need to be…
Blast is a layer-2 on Ethereum launched at the end of 2023, offering interest rates for staking ETH and stablecoins. The TVL of this layer-2 skyrocketed to $2.3 billion within just three months, fueled by the promise of an airdrop.
Recently, another game project on Blast, Super Sushi Samurai (SSS), was also exploited, draining $4.6 million in assets and causing the token price to crash to zero. However, this incident was discovered to be carried out by a white-hat hacker who committed to returning the funds to the developers.